Tinder Bitcoin Scams and Other Crypto Hustles to Avoid
With the Bitcoin price now entering a bull run cycle, Tinder Bitcoin scams and a range of other crypto rip-offs are on the rise - here's what to look out for.
The pseudonymous and hard-to-trace nature of cryptocurrencies makes them a popular target for cybercriminals. Stealing money out of someone’s bank account and getting away with it is hard. Receiving Bitcoin from someone’s crypto wallet once it has been compromised or social engineered, and getting away with it, is easy.
Tinder Bitcoin Scams
Tinder Bitcoin scams and other crypto hustles remain prevalent and scammers are using increasingly creative methods to get their hands on your coins.
An ongoing crypto scam that continues making the rounds can be found on the dating app Tinder. According to a Reddit post, one version of this scam involves Asian women (more likely individuals posing as Asian women) gaining the trust of their victims on Tinder before moving the conversation to Whatsapp or WeChat. Then the conversation turns to investments and “an inside tip about a new crypto asset” or the girl’s rich uncle who is a blockchain investor etc. Once the victims transfer funds, their money is gone. Hundreds of Tinder users have shared their experience in this Reddit post and others – although none say they actually fell for it.
Tinder user ‘John’ shared his Tinder experience with “Zhang Yu” with Brave New Coin. Although scams like this are often referred to as ‘Chinese crypto scams’, the reality is they can be launched from anywhere. “She claimed to be from Qingdao China,” John says, “but her number was recognized as being in Bangkok. Her WhatsApp number was supposedly Chinese, but I know that WhatsApp doesn’t work in China. She poses as the daughter of a rich vineyard owner and sends pictures of her flashy lifestyle.”
John says the conversation quickly turned to crypto. “She gave this website – ghvcoin.com – and persistently asks to register and start trading. She’s adamant that she earns easy 10K, 20K, 40K, every day from trading GHVcoin.” John says he did his homework. “The GHV website does not provide any company registration details – no team behind the project – no physical address – I’m sure it’s just built to receive BTC and ETH deposits.”
An even more sinister version of this scam involves real women targeting crypto holders on Tinder by drugging them and then attempting to drain their crypto accounts. Jameson Lopp, CTO at Casa tweeted that a high net worth Casa client was recently targeted in this way.
YouTube Crypto Scams
On YouTube unfortunately, seeing is not necessarily believing, as the world’s most popular video-sharing platform remains unable to stop fake ads targeting users with an interest in genuine crypto-related video content (BNC’s own channel is often targeted). What makes these scams more convincing is that they include video of trusted crypto notables like ex-Binance CEO Changpeng Zhao and Vitalik Buterin in their scam ads.
Typically the ads will promote some type of Bitcoin or Ethereum ‘giveaway’ with users being asked to send in their BTC and ETH and receive double that back as some type of exchange ‘goodwill’ airdrop. Regrettably, because they appear on a trusted platform like YouTube, people do fall for these scams. In one recent example, Blockchair found that the Bitcoin wallet address shown in a “5000 BTC Giveaway” scam made US$5000 in a matter of days.
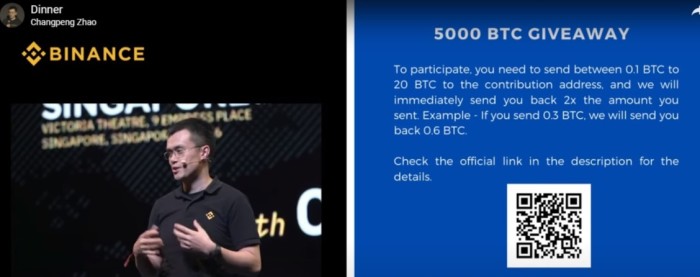
Another similar scam featuring Bitmex recently pulled in $20,000 in BTC in three weeks. Google asks that users report any scam YouTube ads using this form.
Also on YouTube in the comments section of legitimate crypto videos are the ever-present helpful traders who share their success stories and links to the trading gurus who showed them how to do it. 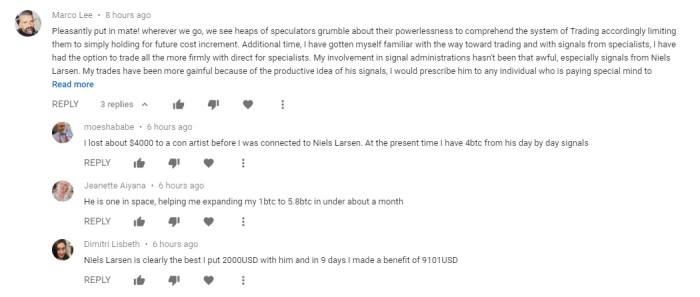
They use an easily spotted technique of one initial poster – and then 5 – 10 replies, from others, usually thanking them for their kindness or sharing their own story of millions earned with Guru Bill’s help. The posts are made by bots and all the ‘people’ are fake. Indeed, if Guru Bill does exist he will definitely make more money from you than you will from him.
SIM Swapping
SIM swapping, also known as SIM jacking, refers to hackers activating your mobile phone number on a device they own to gain access to your email accounts to then access your cryptocurrency exchange accounts and online wallets. Unfortunately for crypto investors, it is still way too easy for hackers to bypass mobile carrier operator’s security protocols to gain access to your mobile number and a SIM card they control.
Unfortunately, telco phone support staff are underpaid and overworked and are not well-trained against sophisticated social engineering attacks. All of the information an attacker needs to know to begin a social engineering attack can be purchased on the dark web. Haseeb Awan, CEO of efani – America’s most secure and private cellphone service, was a recent guest on Brave New Coin’s Crypto Conversation podcast. Listen to the podcast to hear Awan’s advice for crypto holders wanting to mitigate against SIM swap attacks.
Digital asset investor, Michael Terpin, reportedly lost 1,500 BTC in January 2018 after falling victim to SIM swapping. His phone was compromised and the hacker made off with around $24 million worth of cryptocurrency at the time. Even former Twitter CEO Jack Dorsey was not safe from SIM swapping. He reportedly fell victim to this type of hack in August 2019.
While it is difficult to prevent these attacks once someone gets their hands on your mobile phone number – as the point of failure lies with the mobile carrier – you can make use of other two-factor authorization methods to better protect your exchange accounts. Your long-term crypto asset holdings should always be kept in cold storage, in which they are safe from SIM swap attacks.
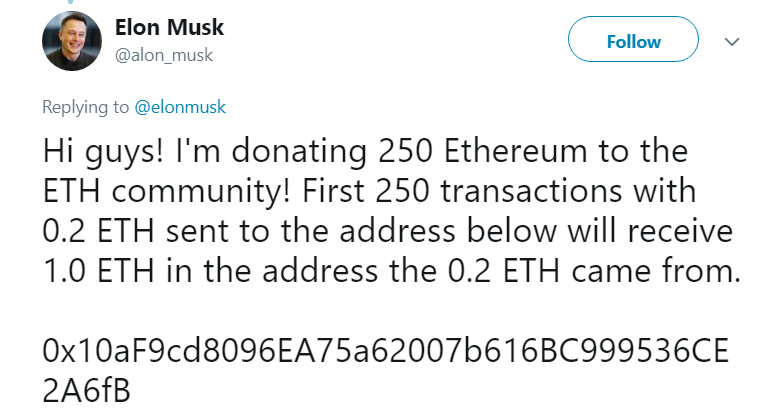
Fake X (Twitter) giveaways
Yes, fake giveaways on lookalike crypto Twitter accounts remain a thing. Twitter has struggled to effectively tackle this issue but has made some progress. Twitter’s algorithms appear to be much more effective at blocking the majority of crypto scammers, however, some are still succeeding.
One typical tactic is that scammers will impersonate a high-profile account such as Elon Musk, using verified Twitter accounts. To do this, scammers gain control of another verified account and then change the profile to impersonate Elon Musk. They then place replies under legitimate Musk tweets and direct users to fraudulent scam websites. As the images below show, many of these attempts appear obvious, even amateurish to most Twitter users, but they are designed to fool non-native English speakers, which they often do.
Crypto Mining Malware & Ransomware
Unauthorized web-based cryptocurrency mining, commonly referred to as cryptojacking, boomed in late 2017 after the launch of the first web-based (and now defunct) Monero miner, CoinHive. Crypto mining malware infects a website and uses its computing power to secretly mine Monero.
The crypto mining malware boom may be over but cybercriminals are still utilizing low-risk, revenue-generating malware, according to Webroot’s Nastiest Malware 2020 report.
Webroot has previously identified two nasty crypto mining malware variants as HiddenBee and Retadup. Hidden Bee uses images and video files to infiltrate computers and use their CPU power to mine cryptocurrency. Retadup was a malicious worm that infiltrated over 850,000 machines with crypto mining software.
While cryptojacking is relatively easy to spot on a computer (as the PC will slow down and heat up), it is not so easy to spot on mobile phones. If your phone is overheating, or your battery is emptying faster than usual, you may have been hit with crypto-mining malware.
Ransomware attacks are continuing to grow in frequency and ransom size. Attackers in this instance will almost always ask for payment in crypto. A high profile attack in the United States targeted hospitals – hampering their efforts to care for patients during the Covid-19 pandemic by threatening to shut down the computer systems that operate a range of medical apparatus. The destructive payload delivered by a ‘TrickBot’ infection is wide-ranging, described by US cyber security experts as “a full suite of tools to conduct a myriad of illegal cyber activities.” These activities include crypto mining, credential harvesting, mail exfiltration, point-of-sale data exfiltration, and the deployment of Ryuk and Conti ransomware.
FINCEN has released guidance warning that ransomware victims themselves may be breaking the law if they pay the ransom. This US Cyber Security alert has full technical details of the latest attack by Conti, TrickBot, and BazarLoader along with recommended prevention and mitigation tactics.
With ransomware attacks growing in scope and severity, the Biden administration is considering a range of options to stem the growing threat reports Politico. Cloud mining is another very common crypto scam. In fact, we wrote a dedicated feature on how to spot these scams, but really the easiest approach is to consider ALL cloud mining to be a scam until you have reputable evidence they’re not.
Corporate identity scams
Corporate identity scams have been around for years but they are easier than ever to pull off when business is conducted via email or some other platform, and convincing looking copycat websites are easy to build. One corporate identity scam doing the rounds in the crypto space at the moment is an advertising offer purportedly coming from CoinMarketCap and advertising aggregator Coinzilla. The scam promises advertisers will receive a huge bonus campaign for booking advertising with CoinMarketCap, stating “Launch a campaign with a budget of 500-50000 USD and receive boost traffic worth the same amount to your Coinzilla account for spending!”
Coinzilla has advised that the promo is scam – and warns that the fake offer may not be the actual point of the scam, but instead the attack is designed to get users to take an action that may infect their computers. “Do not respond to these emails and do not provide the sender with any personal or financial information. Avoid clicking on links included in the email or on attachments, as doing so may result in malware or a virus being loaded on your computer.”
Be careful out there.
Further Reading

Don’t miss out – Find out more today